Understanding the YubiKey: A Distilled Introduction
Motivation
If you are reading this it is likely that you have already heard of Yubico's YubiKey.

You might have come across it after announcements from Google, Github and others declaring that they now support a stronger second factor authentication option called FIDO Universal 2nd Factor or U2F. Great! You know you want better security, especially better security that is easy to use!
So, you did a little deeper...
tl;dr
The YubiKey is a small, rugged, nearly indestructible keychain sized USB device that is able to securely store secrets and perform a number of cryptographic operations on behalf of the user. These cryptographic operations serve as the foundation of the advertised features of the YubiKey which I would categorize into two general buckets:
Multi-factor authentication (MFA) features
Specifically Universal 2nd Factor (U2F), OATH TOTP and HOTP, and Yubico OTP, and
Smartcard features
Specifically OpenPGP and PIV/X.509 based encryption and signing.
Since these features are implemented in a hardened USB device, the secrets for securing your online identity are much safer from rouge third-parties compared to a computer or mobile phone alone.
Goal
In this series of posts I will distill the many things I've learned while trying to grok the YubiKey and it's related security features. In this post I will introduce the YubiKey's features, use-cases, and relevant software just enough to allow a reader to decide if and how they want to use the YubiKey.
If there is interest, in later posts I will go into more technical detail about the security related features and their associated algorithms.
My Journey to YubiKey
If your experience getting started with YubiKey was anything like mine, it went something like this:
(**WARNING** this is a very non-distilled personal anecdote with some griping)
Great, I saw the announcement, I know I want security...I want a YubiKey! So I click to the YubiKey page and... woah! There are 4 devices! Which one do I need? The 4? The 4 Nano? The Neo? or the U2F key? I guess I came here for U2F but the features on the other keys are so enticing! "Strong crypto" and "touch-to-sign" sound like things I want...but the friction of these decisions have exhausted my energy to impulse buy. I file it away as sometime to revisit in the future.
...FUTURE...
I come across another YubiKey related announcement. Oh yeah, I want a YubiKey! Oh yeah, I don't know which one...too many choices. The 4 looks to be the newest so I'll get that one. Awesome!
...FUTURE...
I got my YubiKey! Let me set it up! The packaging directs me to this URL: http://yubi.co/4
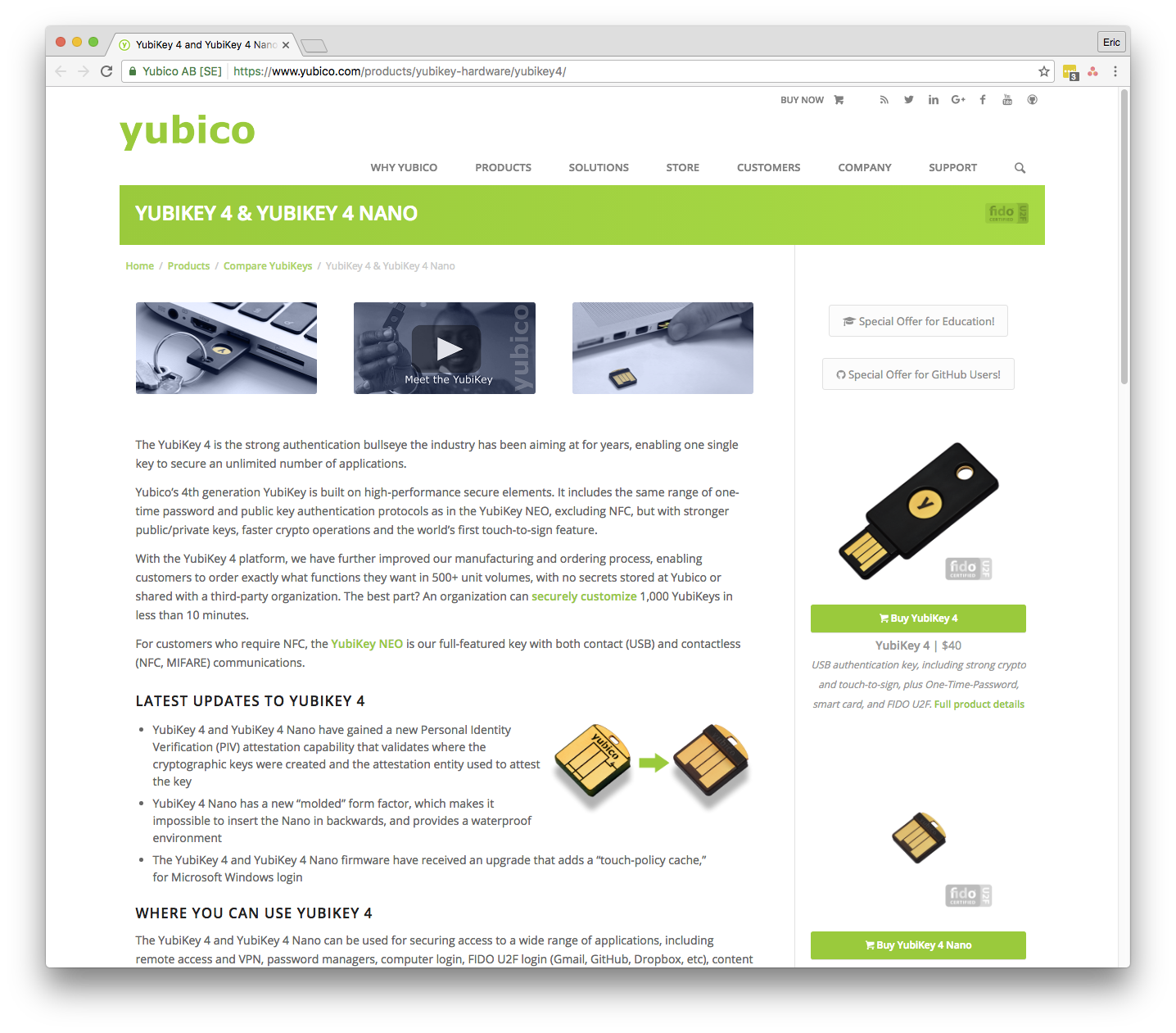
The video gets me excited but this welcome page doesn't really help me start using my YubiKey. :( It directs me to the developer site...but I don't know what I would develop for the YubiKey because I still don't understand what it really is/does! Okay, I'll put it aside for now. I can revisit this in the future...
...FUTURE...
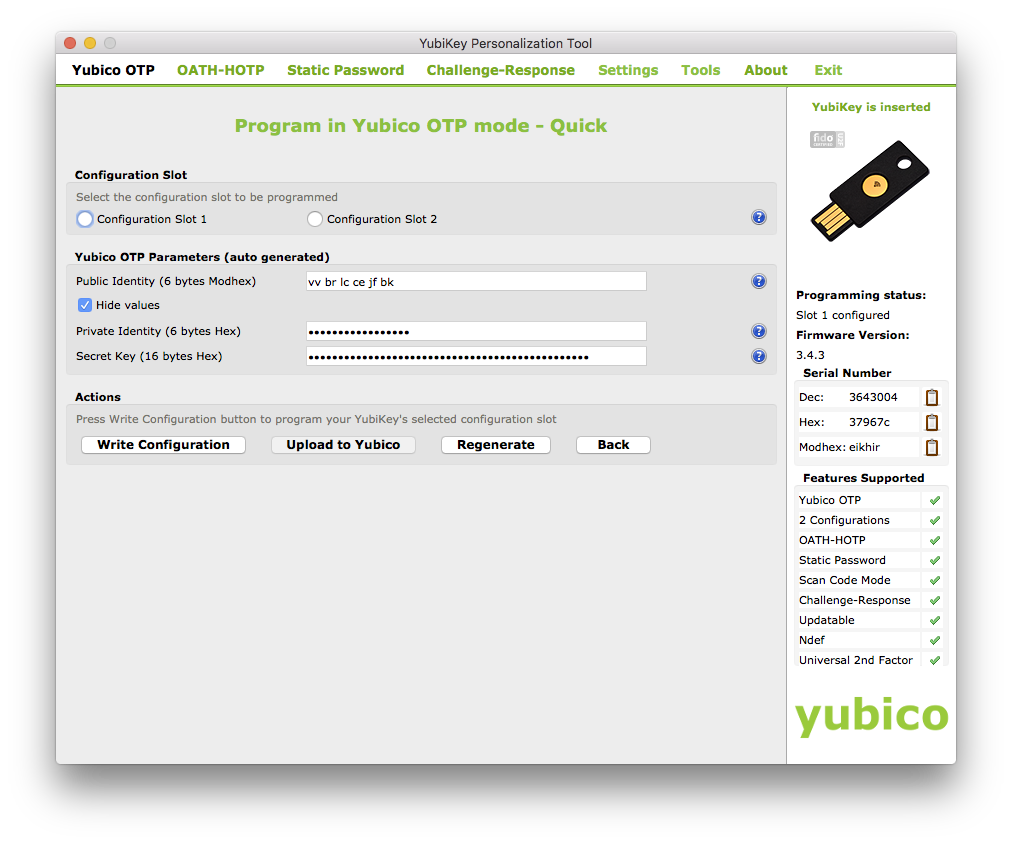
I have some free time, let me try to use that YubiKey thing again! A lot of the videos mention something called the "personalization tool". Okay, I'll get that! Uh oh! This is the most overwhelming piece of software I've ever seen! This looks like some sort of internal diagnostic utility not an end-user program. I am going to break this thing, I know it.

I could go on and on. Perhaps my path is atypical. For me, the YubiKey was something I wanted to integrate into my life as a security best-practice but I kept hitting roadblock after roadblock on a path that was further slowed by headache inducing cognitive friction. In hindsight, I believe everything you need to know to take full advantage of the YubiKey is indeed available on the Yubico site it just wasn't the easiest thing for me to assimilate.
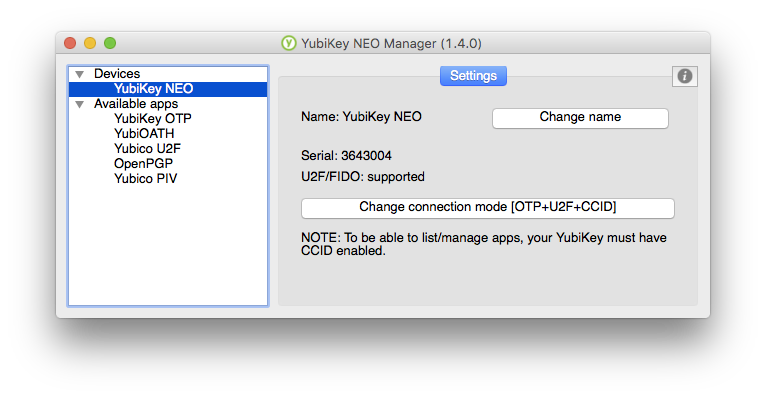
The Device
As mentioned, the YubiKey is a small, lightweight USB device. As of this writing (August 2016), there are currently 3 generations being sold:
- YubiKey 4
- YubiKey NEO
- FIDO U2F Security Key
The YubiKey 4 comes in two form-factors. One form-factor is a keychain fob sized device with dimensions 18mm x 45mm x 3mm (approx 0.7in x 1.8in x 0.1in). It can live on your keychain or in a desk. The other form-factor is smaller at 12mm x 13mm x 3mm (approx 0.5in x 0.5in x 0.1in) and is intended to semi-permanently reside inside of a USB port on your computer. This is useful if you intent to use the YubiKey a lot and would rather not have to plug it in multiple times a day. The downside though is that it monopolizes an entire USB port, which on Macbooks are at a premium. The two form-factors have exactly the same features and capabilities.
The YubiKey 4 feature-wise is a superset of the YubiKey NEO, specifically more encryption and more storage but with two notable exceptions:
(1) the NEO supports communicating via NFC in addition to USB which allows it to communicate with NFC enabled Android phones. This is a very compelling feature if you want to bring your YubiKey MFA protections to services that you use on your Android phone. This is in stark contrast to iOS which the YubiKey is effectively worthless with.*
(2) The YubiKey NEO is somewhat open source with it's use of freely available Java Card applets hosted on Github while the YubiKey 4 is not open source at all. People are varied with their reaction to this change; some have stopped recommending YubiKey altogether while Yubico argues there is a conflict between providing the most secure YubiKey and being open source. There are a lot of finer details relevant to this discussion so I recommend that anyone who is sensitive to the fact that the YubiKey 4 is closed-source read up on the discussions taking place.
The FIDO U2F Security Key is a simpler and cheaper device that only implements the U2F features described below.
This document focuses on the functionality provided by the YubiKey 4 and YubiKey NEO.
All devices have a single, capacitive touch surface on them. On the keychain form-factor it is the circular golden metallic indentation on the top surface of the device. On the Nano form-factor the touch surface is the curved end that protrudes slightly from the USB port. It is important to note that these touch sensors are not biometric in any way. They don't do fingerprint identification or anything like that. They are used because many of the YubiKey's features are initiated by a touch gesture or the feature requires a user to touch to device to confirm/allow an operation.
Features Overview
I think the YubiKey's features are best understood as falling into one of two categories: Multi-factor authentication (MFA) related features, and Smartcard related features.
Multi-Factor Authentication (MFA) features include:
- Yubico OTP
- Universal 2nd Factor (U2F)
- OATH-TOTP
- OATH-HOTP
- Challenge / Response
Smartcard features include:
- OpenPGP
- PIV/X.509
The YubiKey also supports a feature called Static Password which I won't go into in this post. See the YubiKey Personalization Tool for more information.
Multi-factor Authentication Features
The majority of the press you've seen about the YubiKey probably focuses on features related to multi-factor authentication (MFA), specifically U2F and Yubico OTP. The YubiKey also supports time based one-time passwords (TOTP) and event based one-time password (HOTP). In these MFA use-cases the YubiKey can augment or replace the mobile app or SMS messages that may currently be used.
In the context of web authentication, multi-factor authentication is way to further secure user authentication to a site or service by requiring a personalized and unique code from a user in addition to their traditional static password. While static passwords are relatively easy for bad-actors to acquire (through phishing and/or malware), the secrets that generate these unique MFA codes don't readily leave the device they were generated on and thus are much harder to be duplicated and/or exploited by a third-party.
Different MFA algorithms use different pieces of information to generate their codes. I will briefly explain key aspects of each algorithm that the YubiKey supports.
Universal 2nd Factor (U2F)
Universal 2nd Factor (U2F) is a standard started by Google and Yubico as a modern MFA strategy that is easier for the user to use while providing higher security guarantees that other MFA techniques. The user experience on a U2F enabled site is such that after a user enters their password the user is directed to press the capacitive touch sensor on the YubiKey to finish authenticating. Behind the scenes, the YubiKey is generating a cryptographically secure value to authenticate the presence of the YubiKey.
The user experience of U2F is similar to Yubico OTP described below but with a key difference: U2F requires browser support to facilitate connecting to and using the YubiKey. Currently Google Chrome is the only mainstream browser to support U2F out of the box. Yubico OTP doesn't require browser support.
U2F is currently supported by the following services:
- Google (Drive, YouTube, Wallet, Google )
- Github
- Dropbox
- and a few others
The YubiKey works out of the box as a U2F device. No user configuration or intervention is required.
The specifics of how U2F works, how it is implemented, and how it is stronger than other MFA strategies is beyond the scope of this post but if you're interested Yubico has a very readable technical introduction to the U2F protocol.
Yubico OTP
Yubico OTP is a MFA strategy that utilizes a long 44 character string as the one-time password (OTP). An example of a Yubico OTP string is below: